How To Use John The Ripper Windows 10
John the Ripper (JtR) is one of the hacking tools the Varonis IR Team used in the first Live Cyber Assault demo, and 1 of the most pop password neat programs out there. In this weblog mail service, nosotros are going to dive into John the Ripper, prove yous how it works, and explain why it'south important.
Notes about hacking: Hacking is a pursuit of cognition nigh systems, design, and humans. In this instance, we are talking about software and operating systems.
Get the Free Pentesting Active Directory Environments e-volume
Hacking is not necessarily criminal, although it can be a tool used for bad intentions. We advocate for upstanding hacking. Stay in the lite side of the Force.
How Does John the Ripper Work?
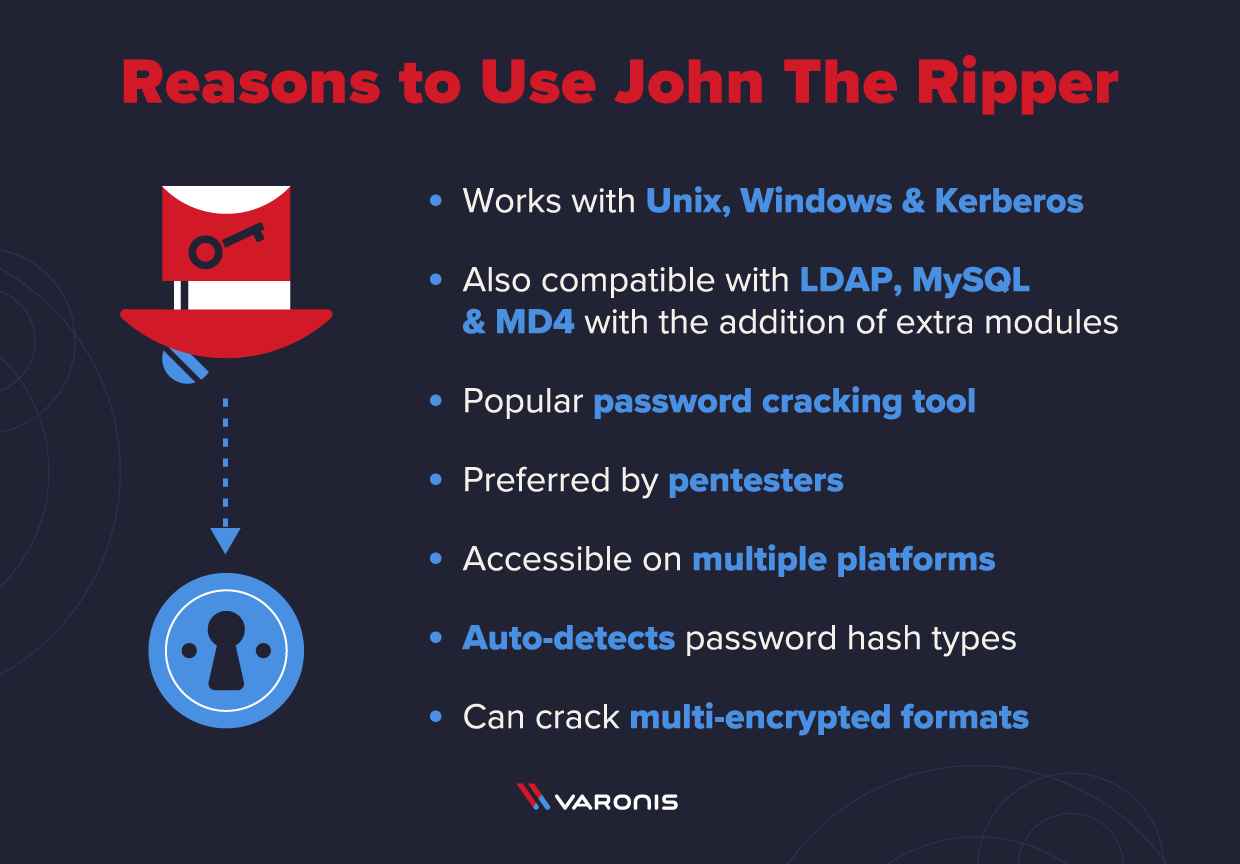
JtR supports several mutual encryption technologies out-of-the-box for UNIX and Windows-based systems. (ed. Mac is UNIX based). JtR autodetects the encryption on the hashed data and compares information technology against a large plain-text file that contains popular passwords, hashing each password, and then stopping information technology when it finds a match. Uncomplicated.
In our amazing Alive Cyber Attack demo, the Varonis IR team demonstrates how to steal a hashed password, use JtR to find the truthful password, and apply it to log into an authoritative account. That is a very common use example for JtR!
JtR besides includes its ain wordlists of common passwords for 20+ languages. These wordlists provide JtR with thousands of possible passwords from which information technology can generate the corresponding hash values to make a loftier-value gauge of the target password. Since most people choose easy-to-retrieve passwords, JtR is oftentimes very effective even with its out-of-the-box wordlists of passwords.
JtR is included in the pentesting versions of Kali Linux.
What is John the Ripper Used for?
JtR is primarily a countersign cracker used during pentesting exercises that tin help It staff spot weak passwords and poor password policies.
Here is the list of encryption technologies institute in JtR:
- UNIX catacomb(three)
- Traditional DES-based
- "bigcrypt"
- BSDI extended DES-based
- FreeBSD MD5-based (linux and Cisco IOS)
- OpenBSD Blowfish-based
- Kerberos/AFS
- Windows LM (DES-based)
- DES-based tripcodes
- SHA-crypt hashes (newer versions of Fedora and Ubuntu)
- SHA-crypt and SUNMD5 hashes (Solaris)
That's the "official" list. JtR is open-source, then if your encryption of choice isn't on the list do some excavation. Someone might have already written an extension for it.
How to Download John the Ripper
JtR is an open-source project, and then you tin either download and compile the source on your ain, download the executable binaries, or observe it as part of a penetration testing package.
The official website for John the Ripper is on Openwall. You tin can grab the source code and binaries there, and you tin join the GitHub to contribute to the project.
JtR is available on Kali Linux as part of their password cracking metapackages.
Tutorials for Using John the Ripper
We are going to get over several of the basic commands that you lot need to know to start using John the Ripper. To get started all yous need is a file that contains a hash value to decrypt.
If yous ever need to encounter a list of commands in JtR, run this command:
.\john.exe
Cracking Passwords

John the Ripper's primary modes to crack passwords are single crack way, wordlist way, and incremental. The single crack style is the fastest and best mode if you lot accept a full password file to crevice. Wordlist mode compares the hash to a known list of potential password matches. Incremental mode is the virtually powerful and possibly won't consummate. This is your classic creature strength mode that tries every possible grapheme combination until you have a possible result.
The easiest way to try swell a password is to permit JtR go through a series of mutual cracking modes. This control below tells JtR to effort "simple" way, then the default wordlists containing likely passwords, and so "incremental" fashion.
.\john.exe passwordfile
Yous can also download different wordlists from the Net, and you can create your own new wordlists for JtR to use with the –wordlist parameter.
.\john.exe passwordfile –wordlist="wordlist.txt"
If you lot want to specify a cracking way use the exact parameter for the mode.
.\john.exe --unmarried passwordfile .\john.exe --incremental passwordfile
Word Mangling Rules
Mangling is a preprocessor in JtR that optimizes the wordlist to make the peachy process faster. Employ the –rules parameter to set the mangling rules.
.\john.exe --wordlist="wordlist.txt" --rules --passwordfile
Viewing Your Output
When yous want to see the list of passwords that you lot have cracked, utilize the –show parameter.
.\john.exe –show passwordfile
If your cracked password list is long, you lot can filter the listing with additional parameters. You tin can too redirect the output using basic redirection in your shell. For example, if you want to encounter if you cracked whatsoever root users (UID=0) apply the –users parameter.
.\john.exe --show --users=0 passwordfile
Or if yous want to show users from privileged groups use –groups.
.\john.exe –-show –-groups=0,i passwordfile
Beneath is the JtR command from our Live Cyber Assail Webinar. In this scenario, our hacker used kerberoast to steal a Kerberos ticket granting ticket(TGT) containing the hash to be cracked, which was saved in a file called ticket.txt. In our case, the wordlist used is the classic rockyou password file from Kali Linux, and the control was gear up to report progress every 3 seconds.
.\john.exe "--format=krb5tgs" "ticket.txt" "--wordlist="rockyou.txt" "--progress-every=3"
If yous want to see some cool pentesting and defense tactics using Varonis, bank check out the Live Cyber Attack Webinars! Pick any time that works for yous!
How To Use John The Ripper Windows 10,
Source: https://www.varonis.com/blog/john-the-ripper
Posted by: gillmandifuld.blogspot.com


0 Response to "How To Use John The Ripper Windows 10"
Post a Comment